The Incident: A Silent Website Takeover
In September 2024, a Hong Kong law firm experienced a web defacement attack that went unnoticed for days. The firm had just migrated its website to a new hosting provider — without endpoint detection, logging, or antivirus protection in place.
This gap gave an attacker the opening to abuse a vulnerable WordPress plugin, upload malicious scripts, and alter the firm’s online presence. Search engine results began returning abnormal metadata, while persistent backdoors were planted deep inside the server.
How Attackers Got In: Webshells, SEO Poisoning, and Plugin Exploits
Upon activation of Blackpanda IR-1, our incident responders quickly uncovered the attacker’s methods:
- Multiple obfuscated PHP scripts uploaded into plugin directories
- Modified landing pages and poisoned SEO metadata
- Backdoors disguised as text files and JavaScript
- Malicious edits to the .htaccess file enabling persistence
- DNS changes to maintain hidden access
Although no files were destroyed or encrypted, the incident significantly impacted brand reputation and search visibility.
IR-1 in Action: Rapid Containment and Backdoor Removal
Because the law firm was an IR-1 subscriber, Blackpanda’s elite DFIR team was mobilised the same day. Investigators:
- Conducted live triage and forensic analysis of the server
- Identified and removed all hidden PHP backdoors
- Isolated the compromised web instance to prevent further spread
- Provided tactical recovery steps to restore normal operations
Key Findings:
- Multiple PHP backdoors enabled arbitrary attacker commands
- SEO poisoning aimed at hijacking visibility
- No lateral movement or internal data theft detected
- No attribution to a known APT or threat actor group
“We had just completed a major website migration. IR-1 helped us understand what happened and secure everything again — fast.”
— IT Director, Hong Kong Law Firm
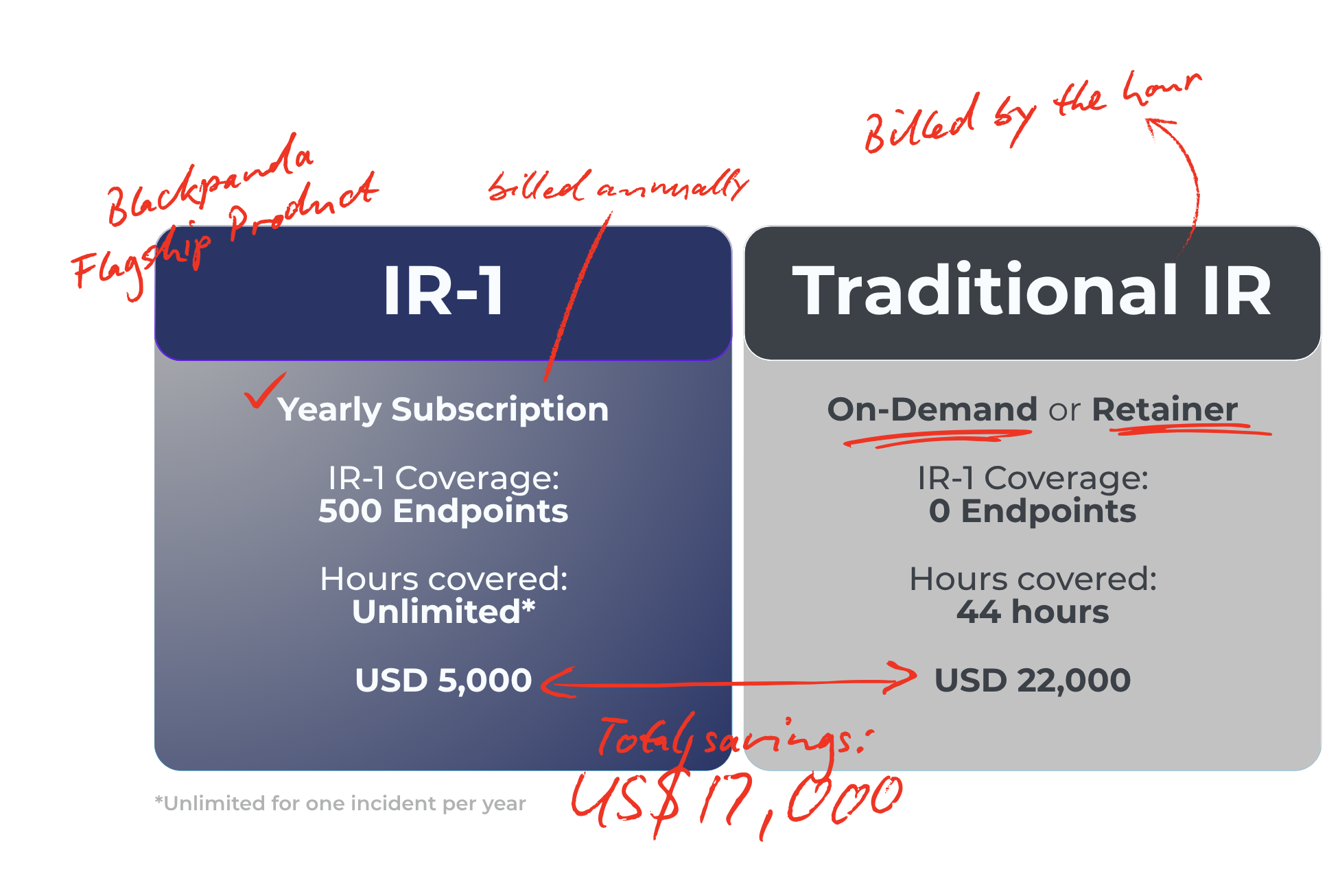
Cost Savings Snapshot
What Could Have Happened Without IR-1
Without IR-1, the law firm risked:
- Delayed discovery and extended exposure
- High, unpredictable IR consulting bills
- Missed detection of hidden backdoors
- Prolonged reputational harm from poisoned search listings
Instead, IR-1 delivered same-day expert response, complete containment, and lasting web hardening.
Beyond the Response: Long-Term Protection
Blackpanda’s team guided the law firm through post-incident hardening:
- Deployed partner EDR on the compromised server
- Restored clean web backups and aligned DNS
- Secured plugins and upgraded WordPress
- Hardened .htaccess and web root permissions
- Applied IP filtering and WAF for future protection
- Restored clean SEO metadata to repair online visibility
Frequently Asked Questions
1) What happened in this incident?
A Hong Kong law firm’s public website was hijacked after attackers exploited a vulnerable WordPress plugin during a recent hosting migration. They altered SEO metadata, planted obfuscated PHP backdoors/webshells, and modified .htaccess to maintain persistence. Blackpanda IR-1 responders contained and remediated the compromise within hours.
2) Was any client data stolen?
There were no signs of lateral movement or internal data exfiltration. The impact centred on website integrity, search visibility, and brand reputation rather than encrypted or destroyed files.
3) How was the breach detected?
The firm noticed abnormal search listings (poisoned metadata) two days after go-live. On activating IR-1, Blackpanda performed live triage and forensics, uncovering malicious scripts and persistence mechanisms across plugin directories and the web root.
4) What were the attacker’s persistence methods?
Obfuscated PHP files, disguised webshells (e.g., .txt masquerades), altered index.php, rogue JavaScript, .htaccessexecution allowances, SEO poisoning, and DNS changes that supported ongoing access.
5) What immediate steps did Blackpanda take?
Same-day mobilisation under IR-1: isolating the affected instance, identifying and removing backdoors, reversing SEO tampering, validating DNS, and guiding safe recovery and hardening.
6) What hardening actions were implemented post-incident?
Deployment of EDR on the server, restoration from clean backups, plugin security review and WordPress upgrade, stricter web root permissions, .htaccess hardening, IP filtering/WAF, and an SEO repair plan.
7) Could this have been prevented?
Many risks stemmed from migration without logging/EDR and an unpatched plugin. Enforcing a change/migration checklist, continuous monitoring, least-privilege file permissions, and web application protections would have significantly reduced exposure.
8) How fast is IR-1 response compared to traditional IR?
IR-1 enables same-day expert engagement with pre-agreed workflows, avoiding delays from scoping, contracting, and procurement typical of ad-hoc consulting.
9) What did the firm save by using IR-1?
The firm avoided unpredictable hourly fees (e.g., an estimated USD 22,000 for a comparable 44-hour engagement) and minimised reputational harm through rapid containment and restoration.
10) What should organisations do after a defacement or SEO poisoning?
Activate incident response immediately, snapshot and isolate assets, collect logs/artifacts, remove persistence, restore from known-good backups, rotate credentials, review DNS and CDN/WAF configurations, and repair search metadata to mitigate reputational impact.
Already an IR-1 Customer? You’re Covered.
As an IR-1 subscriber, you already have 24/7 access to Asia’s leading cyber incident responders, backed by Lloyd’s of London.
Your subscription includes:
- Always-on access to Blackpanda’s DFIR team
- Continuous Attack Surface Readiness (ASR)
- Discounted, pre-integrated cyber insurance
Cyber emergency? IR-1 puts elite response just a few clicks away.









