Date of Incident: May 16, 2025
MSSQL Exploitation and Remote Access Detected
The compromise began with brute-force attempts against a Microsoft SQL Server exposed to the internet. Between late April and early May, the company’s system recorded over 50,000 failed login attempts from Russian IPs. The attackers eventually gained access—most likely through weak credentials or an unpatched MSSQL vulnerability.
Once inside, the attackers:
- Enabled Microsoft SQL’s Common Language Runtime (CLR) to run unsafe .NET assemblies
- Used the CLR to inject and execute trojan malware via memory
- Established interactive access to the host using Remote Desktop Protocol (RDP) from a German VPN IP
The attack was precise. All activity was confined to a single server with no evidence of spread to other internal systems. However, within hours, over 50,000 files had been encrypted, and a ransom note was dropped.
ODIR in Action: Evidence-Based Response at Speed
While the company was not an IR-1 subscriber at the time, Blackpanda’s On-Demand IR (ODIR) engagement brought full DFIR capabilities to bear:
- Forensic imaging of affected server memory and disk
- Attack timeline reconstruction showing SQL CLR abuse, RDP access, and ransomware execution
- Analysis of persistence attempts, defense evasion, and tooling (including Process Hacker, SoftPerfect Scanner, and custom .NET malware)
- Confirmation that no data exfiltration had taken place
Though the Bixi ransomware was successfully deployed, the attacker did not maintain persistence, nor were any credentials or documents exfiltrated.
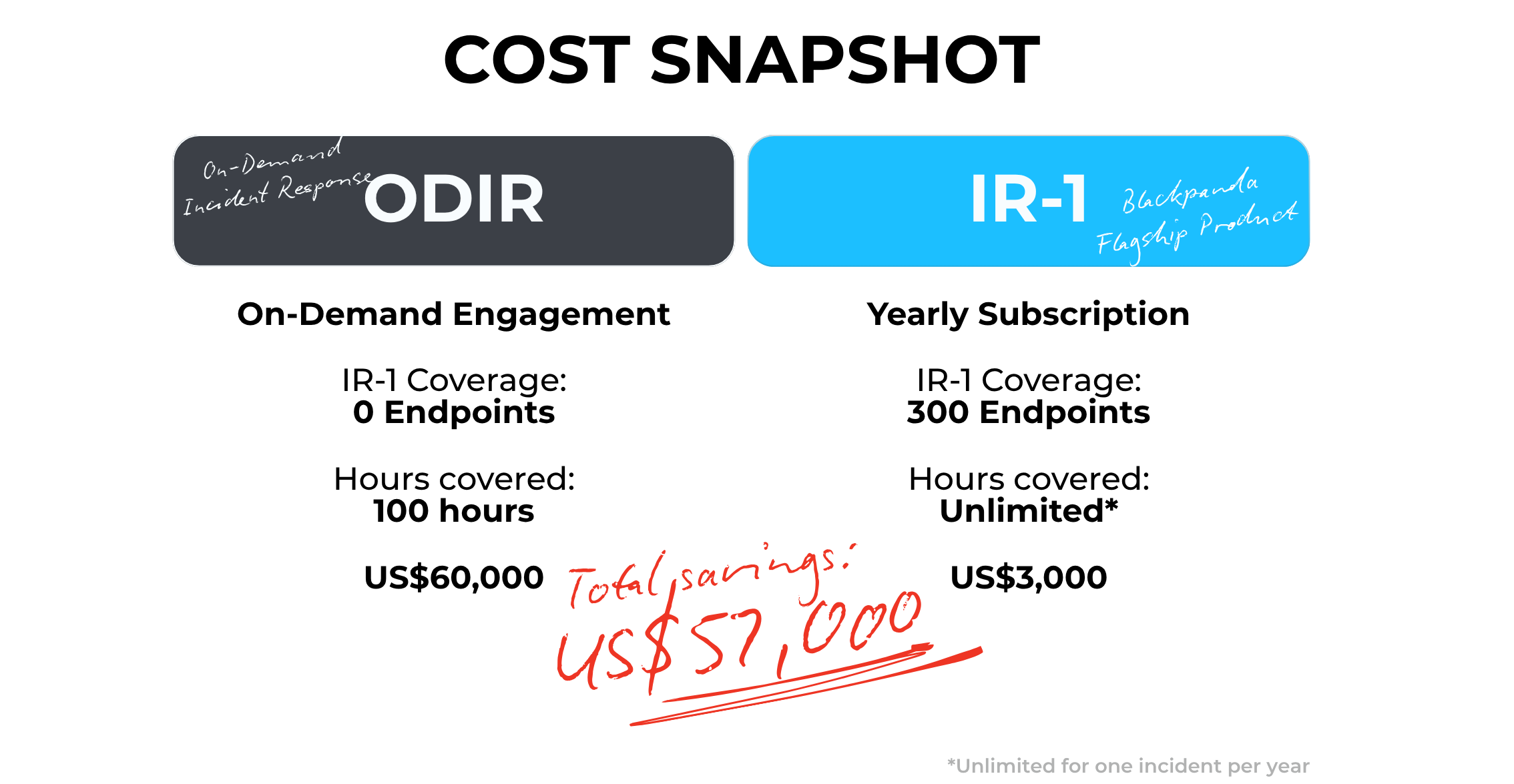
What IR-1 Would Have Delivered
Had the company been subscribed to IR-1 at the time, they would have benefited from:
- Zero-cost, on-demand triage via the IR-1 console
- Pre-deployed EDR and telemetry pipelines
- Attack Surface Management (ASM) alerts for exposed RDP
- Peace of mind with integrated cyber insurance options

Instead of post-crisis contracting, IR-1 would have enabled push-button response from day zero. IR-1 eliminates guesswork, contracts, and delays - because response should be automatic.
Post-Incident Remediation
Blackpanda delivered a targeted recovery and hardening plan, including
- Critical:
- Full password reset of all privileged accounts
- Removal of RDP exposure and unnecessary internet-facing services
- Endpoint Detection and Response (EDR) deployment
- Full password reset of all privileged accounts
- High/Medium:
- Implementation of multi-factor authentication
- SQL patching and version hardening
- Network segmentation and improved logging
- Implementation of multi-factor authentication
- Ongoing Risk Reduction:
- Employee cybersecurity training
- Password management and Windows LAPS configuration
- Regular dark web monitoring (multiple credentials were exposed)
- Employee cybersecurity training
For IR-1 Customers
As a reminder, you enjoy the peace of mind of being a Blackpanda IR-1 customer as well. Rest well knowing that the best cyber incident responders in Asia are standing by 24/7 to respond at a moment’s notice when the worst occurs and the attackers are able to make it past even the most well-prepared cyber and IT defenses.
As a Lloyd’s of London-backed insurance underwriting entity, Blackpanda uniquely has productized digital forensics and incident response services into an assurance product delivered via SaaS subscription, complimentary Attack Surface Management technology, and discounted and optimized Blackpanda comprehensive cyber insurance offerings to provide the most cost-effective solution in the event of cyber emergencies.
Reach out via your IR-1 platform access to view your ASM results. To gain an automated price quote on cyber insurance from us, email us at customercare@blackpanda.com and we will promptly get back to you.
Thank you for your continued trust in having Blackpanda ensure you have prompt access to cyber emergency response when the worst happens.
Need help? You're already covered.
As an IR-1 subscriber, you're just a few clicks away from activating Asia’s top cyber emergency response team.
.png)








