Timeline of the Incident
- Date of Incident: October 2024
- Point of Entry: Likely through stolen credentials or leaked API keys
- Fraudulent Activity: High-value gift cards (S$1,000–S$1,500) generated and redeemed online
How the Compromise Happened
Investigations revealed two potential sources of compromise:
- Theft of a Thailand-based IT team member’s Google Password Manager credentials (via phishing or device compromise).
- A ransomware breach earlier in March 2024, during which sensitive API keys were leaked to the darknet.
With access secured, the attackers exploited the internal API to generate gift cards, then attempted multiple redemptions across the group’s e-commerce platforms and mobile app.
Despite lost forensic artefacts due to system reimaging, Blackpanda’s Digital Forensics & Incident Response (DFIR) team reconstructed enough activity to assess root cause and scope.
IR-1 in Action: Forensics, Containment, and Fraud Mitigation
Thanks to Blackpanda IR-1, the Singapore Retail Group received immediate DFIR support. Rapid triage, log correlation, and API analysis pinpointed attacker activity and exposed vulnerabilities.
Key Findings
- Stolen credentials or leaked API keys used to generate gift cards
- No endpoint detection or log retention during the attack window
- System reimaging erased forensic artefacts before investigation
- Multiple vulnerabilities uncovered in web infrastructure via Attack Surface Readiness (ASR) scans
- Exposed admin panels, outdated PHP/nginx, and weak TLS configurations
- Darknet search confirmed multiple compromised IT staff accounts
“Even though we weren’t sure where the compromise began, IR-1 helped us lock things down quickly and keep losses minimal.”
— CISO, Singapore Retail Group
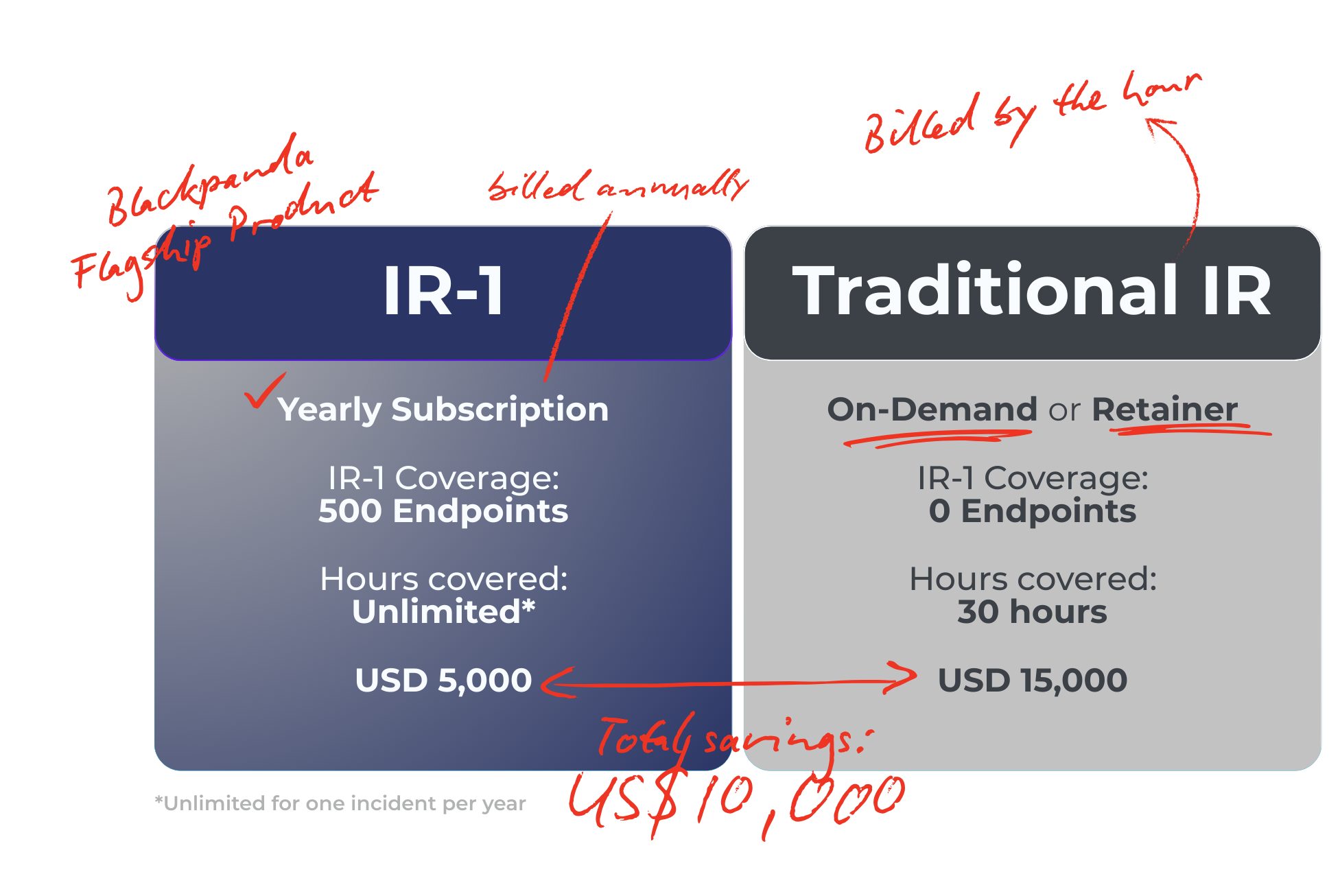
Cost Savings Snapshot
What Could Have Happened Without IR-1
Without Blackpanda’s IR-1 subscription, the group might have:
- Lost S$5,000+ in fraudulent gift card redemptions
- Failed to trace the attacker’s entry point or techniques
- Remained vulnerable to API abuse and admin panel exploitation
- Suffered prolonged fraud activity due to compromised credentials on the darknet
Instead, IR-1 delivered:
- Immediate containment of fraudulent activity
- ASR scans and remediation of vulnerabilities
- Darknet intelligence on stolen staff credentials
- Practical guidance to harden systems and reduce future risk
Beyond the Response: Long-Term Security Improvements
Blackpanda’s DFIR team provided post-incident recommendations that strengthened the client’s cyber resilience:
- Full reset and MFA enforcement for compromised accounts
- Extended log retention for future forensic capability
- IT team awareness training focused on incident response
- Enhanced password management protocols (NIST SP 800-63B aligned)
- Patch management and end-of-life system replacement
- Strategic backup and ransomware recovery planning
- Lockdown of public-facing admin panels
- TLS configuration hardened against legacy ciphers
Frequently Asked Questions
Q1. What was the main attack vector in this case?
Attackers leveraged stolen credentials or leaked API keys to exploit an internal API and generate fraudulent gift cards.
Q2. How did Blackpanda’s IR-1 help?
IR-1 provided immediate incident response, containment of fraudulent accounts, vulnerability scans, and practical recovery guidance.
Q3. What lessons can other businesses learn?
Businesses should enforce MFA, maintain log retention, secure APIs, and subscribe to an IR service like IR-1 for rapid response.
Q4. How much can IR-1 save compared to traditional IR?
Traditional IR consulting can cost upwards of USD 15,000 per incident. IR-1 delivers fixed-cost annual coverage with additional built-in services.
Already an IR-1 Customer? You’re Covered.
As an IR-1 subscriber, you already have 24/7 access to Blackpanda’s elite incident responders, backed by Lloyd’s of London.
Your subscription includes:
- Always-on DFIR support when attacks happen
- Built-in Attack Surface Readiness (ASR) scans
- Access to discounted, pre-integrated cyber insurance
Cyber emergency? You’re already protected.
IR-1 puts elite response just a few clicks away.
👉 Contact: customercare@blackpanda.com







.png)
