The Incident: File Server Offline and Signs of Intrusion
On 1 July 2025, the company reported that its new file server had suddenly become unreachable. During initial triage, Blackpanda identified anomalies including:
- The server disconnecting from the Domain Controller
- Inconsistent firewall logs due to outdated firmware
- Missing DHCP records (the DHCP server was hosted on the compromised server itself)
Because both logging and system state were incomplete due to reformatting, Blackpanda initiated forensic reconstruction using available Windows Event Logs, EDR alerts, and network telemetry.
Initial Access: Attacker Uses Administrator Account
The earliest confirmed malicious activity occurred on 19 June 2025, when suspicious RDP logins targeted a backup server using the local administrator account.
- Timing and pattern strongly indicated compromised staff laptops or misused credentials
- DHCP logs that could map the IPs were unavailable due to system reformatting
Because the initial entry vector could not be determined from available logs, the compromise timeline begins at the first observed unauthorized RDP login.
Lateral Movement: Pivoting to Critical Systems
Once inside, the attacker used the same administrative credentials to RDP into a second server, then escalated activity by creating two unauthorized virtual machines.
Unauthorised VMs Created
Both hosted on the secondary server and used to access other assets using the compromised admin account.
Tooling Observed
- AnyDesk found installed across multiple endpoints, including the rogue VMs
- iDRAC root login observed from a compromised server — indicating attempts to manipulate hardware-level management interfaces
- Suspicious PowerShell command detected by Sophos, consistent with reconnaissance of NIC Teams and Hyper-V virtual switches
This combination of VM creation, credential reuse, and remote access tools pointed to a sophisticated persistence attempt designed to evade EDR visibility by operating inside isolated virtualized environments.
Firewall Limitations and Missing Evidence
The company’s SonicWall firewall (firmware 5.8.1.4 — end-of-life) provided limited telemetry:
- Insufficient detail to detect brute force activity
- Inability to correlate internal IP behaviour
- Two high-volume internal IPs could not be fully accounted for
- Lack of event granularity prevented deep analysis
Combined with one server being reformatted before analysis, the absence of logs restricted full reconstruction of attacker actions.
Possible Credential Exposure on the Dark Web
During the investigation, Blackpanda uncovered multiple corporate credentials associated with the company’s domain that had been leaked on the dark web between 2024 and 2025 — raising the likelihood that the attacker leveraged previously compromised passwords.
Key Findings
- Local administrator account misused for lateral movement
- Unauthorized VMs created for persistence and evasion
- AnyDesk remote access tool installed on key assets
- Suspicious PowerShell command indicating host reconnaissance
- iDRAC root login suggesting deeper privilege exploration
- Outdated firewall limited visibility into attacker behaviour
- Missing logs prevented confirmation of initial entry vector
What Blackpanda IR-1 Contained
Blackpanda executed the following containment measures:
- Reset credentials for compromised administrator account
- Reformatting and rescanning of affected assets
- Isolation of servers showing suspicious RDP or virtualization activity
- Removal of unauthorized VMs and remote access tools
- Identification of high-risk leaked credentials
These efforts successfully halted attacker activity and restored operational stability.
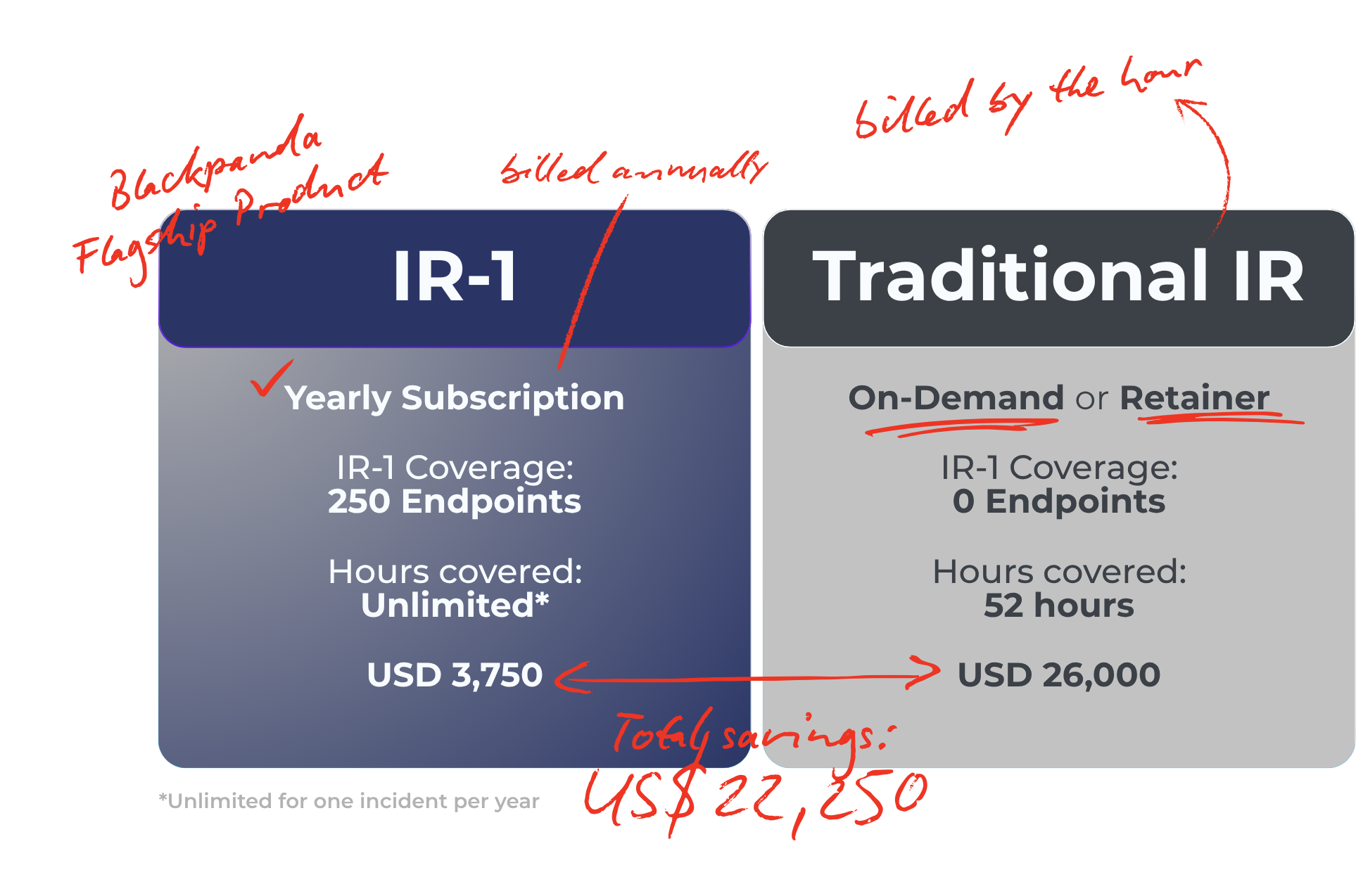
Cost Savings Snapshot
All prices are indicative and subject to change at any time.
What Could Have Happened Without IR-1
Without prompt containment, the company risked:
- Full escalation across critical servers
- Persistent RDP and AnyDesk-based remote control
- Data exfiltration via isolated VMs
- Domain-level compromise
- Introduction of ransomware or further malicious tooling
- Prolonged, invisible persistence due to missing logs and outdated firewall telemetry
Long-Term Resilience: Blackpanda Recommendations
People
- Security awareness training
- Incident response readiness
- Clear accountability for privileged access
Process
- Review and restrict RDP and remote admin policies
- Enforce strong password policies (NIST SP 800-63B)
- Implement Windows LAPS
- Patch management and end-of-life system roadmap
- Routine compromise assessments
Technology
- Continue using SentinelOne EDR
- Upgrade SonicWall to supported firmware
- Enforce MFA everywhere
- Strengthen backup strategy with offline copies
- Periodically test restore processes
Already an IR-1 Customer? You’re Covered.
As an IR-1 subscriber, you already have 24/7 access to Asia’s leading cyber incident responders.
Your subscription includes:
- Always-on access to Blackpanda’s DFIR team
- Attack Surface Readiness (ASR) scans
- Access to faster claims and discounted cyber insurance premiums
Cyber emergency? IR-1 puts elite response just a few clicks away.
Frequently Asked Questions
1) What triggered the IR-1 response?
The company’s newly deployed file server suddenly became unreachable and disconnected from the Domain Controller. During initial triage, this outage revealed suspicious administrator activity and potential signs of compromise, prompting activation of Blackpanda IR-1.
2) How did the attacker initially gain access?
The earliest confirmed malicious activity was suspicious RDP logins targeting a backup server using a local administrator account. Because DHCP and system logs were missing after reformatting, the exact initial entry vector could not be confirmed, but the behaviour strongly suggested compromised staff devices or misused credentials.
3) What lateral movement did Blackpanda observe?
Once inside, the attacker reused the same administrator credentials to pivot to another server, where they created unauthorised virtual machines. These VMs were then used to access other assets, indicating deliberate mapping of the internal network and escalation towards more critical systems.
4) Which tools and techniques did the attacker use to maintain persistence?
The attacker combined several techniques: creating rogue Hyper-V virtual machines, installing the AnyDesk remote access tool on key endpoints, issuing a reconnaissance PowerShell command to profile virtual switches and NIC teaming, and leveraging iDRAC access from a compromised server. Together, these pointed to an attempt to maintain long-term, low-visibility control.
5) Why was the investigation constrained by missing evidence?
One of the main servers had been reformatted before forensic analysis, and the SonicWall firewall was running an end-of-life firmware version with limited logging. The lack of DHCP mappings and granular firewall telemetry restricted Blackpanda’s ability to reconstruct all stages of the compromise.
6) What containment actions did Blackpanda IR-1 take?
Blackpanda reset compromised administrator credentials, isolated and rescanned affected systems, removed unauthorised virtual machines and remote access tools, and helped the company identify high-risk leaked credentials. These steps halted malicious activity and stabilised the environment.
7) Could the attacker have caused further damage without IR-1?
Yes. Without prompt response, the attacker could have extended lateral movement across more servers, exfiltrated data from inside the virtual machines, deployed ransomware or additional tooling, and maintained long-term persistence that would have been difficult to spot given the logging gaps.
8) What are the key recommendations for preventing similar incidents?
Key recommendations include tightening RDP and remote administration policies, enforcing strong password hygiene and Windows LAPS, upgrading SonicWall firmware, enforcing MFA everywhere, strengthening backup and restore testing, and investing in ongoing security awareness and compromise assessments.








